A Billion Blue Screens as Windows is Down Worldwide
A billion computer s worldwide needs to be rebooted in fail mode and have a driver manually. This was a mistake by Crowdstrike, where a bad update of Windows was performed.
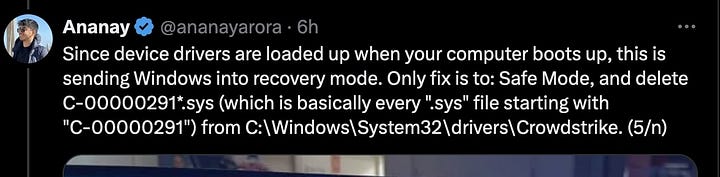
It can be fixed by booting into safe mode and removing the csagent.sys and/or C-00000291*.sys driver.
You will need to have admin access and the drive has to not be encrypted.
To fix the CrowdStrike bad driver problem, you can follow these steps:
Without Encryption:
Boot your Windows system into safe mode or the Windows Recovery Environment (winRE) by first powering up your machine until a manufacturer's logo is visible.
Press the power button again to power up and the machine will boot to the winRE.
From the option menu, select Troubleshoot >> Advanced Options >> Startup Settings >> Restart.
Select option 5 or press F5 to restart the machine in safe mode with Networking.
Wait for the machine to boot into the safe mode desktop.
Open the File Manager and navigate to C:\Windows\System32\drivers\CrowdStrike
Look for and delete any files that match the pattern "C-00000291*.sys"
Reboot as normal.
With Encryption (BitLocker):
If your system is encrypted with BitLocker, you will need to enter the recovery key to proceed with the startup process. Once you have entered the recovery key, you can follow the steps above to delete the problematic driver file.
Remember to be cautious when deleting system files and ensure you have a backup of your important data before making any changes to your system.
If your drive is encrypted then this will be more difficult.

CrowdStrike is a major cybersecurity technology company based in Austin, Texas. They provides cloud workload protection and endpoint security, threat intelligence, and cyberattack response service. They caused a billion blue screens of death with a faulty CrowdStrike software update. Affected machines were forced into a bootloop, making them unusable. The global outage is grounding commercial airline flights, temporarily taking Sky News offline, and even impacting 911 emergency call centers.
The blue screen of death is reported with a stop code of PAGE_FAULT_IN_NONPAGED_AREA from the csagent.sys driver.
A description of the scale of the largest outage ever. I don’t think you guys fully grasp how big this is. Around a billion computers are bricked worldwide, mostly corporate ones. This isn’t just an online service going down for a few hours. Every affected computer needs to be rebooted in fail mode and have a driver manually…
Linux operating system (open source and more secure) supporters are all over twitter and other social media telling windows users. "I told you so".
Crowdstrike Identified as Overvalued Before the Incident
The company, Crowdstrike, is being sold off and Microsoft has also lost about 2%.
Wall Street Bets had some people buy puts against Crowdstrike or short sell Crowdstrike. This was about 12 hours before the outage was caused.
Thesis: Crowdstrike is not worth 93 billion dollars (at time of writing).
Fear: CrowdStrike is an enterprise-grade employee spying app masquerading as a cloud application observability dashboard.
OBSERVATIONS
The 75th percentile retail investor has a tenuous grasp on “Cloud”, “Software Engineering”, and “Cyber Security”.
The median “Cyber Security Analyst” has a tenuous grasp on “Cyber Security”
The median “Software Engineer” has a tenuous grasp on “Cyber Security” and “Cloud”
The median retail investor has a tenuous grasp on “markets” and “liquidity pools”
CRITIQUES
Corporations could buy CrowdStrike to spy on their own employees.
CrowdStrike’s utility is limited- they simply collect all of their customer’s data and display it on a dashboard.
CrowdStrike is dangerous in that they have root access to every device(i.e. endpoint) across thousands of firms.
CrowdStrike customers sign up to get their firm’s data added to a bank which CrowdStrike then has license to use for “correlation”
Keep reading with a 7-day free trial
Subscribe to next BIG future to keep reading this post and get 7 days of free access to the full post archives.





